Some 37,000 people downloaded a spam version of the "AdBlock Plus" extension from Google after a fraudulent ad blocking extension snuck through Google Chrome's verification process and appeared in the Chrome Web Store yesterday.
It's easy to see why Google (and some 37,000 people) were tricked — the developer who packaged the adware into an extension used the name of an already popular and legitimate extension, AdBlock Plus.
SEE ALSO:Whoops, a hacker found a way to steal your passwords from macOS High SierraAdditionally, the bogus page in the Chrome store came with reviews. In short, the fraudulent extension looked pretty realistic. Twitter user SwiftOnSecurity, who regularly tweets about web security, posted an image of the devious extension:
Google allows 37,000 Chrome users to be tricked with a fake extension by fraudulent developer who clones popular name and spams keywords. pic.twitter.com/ZtY5WpSgLt
— SwiftOnSecurity (@SwiftOnSecurity) October 9, 2017
Google eventually caught wind of the breach and removed the deceitful adware, but it remains unclear just how harmful the malware is for those who already downloaded the extension. At least one unfortunate user says they're being hit with ads. In a screenshot of a review, posted by SwiftOnSecurity, the user states that the "instant this was added to Chrome started getting invasive ads with high volume levels opening new tabs."
Though Google took down the adware, SwiftOnSecurity was unimpressed by Google's failure to stop this malware from sneaking through and ending up conspicuously displayed in the Chrome store in the first place:
Legitimate developers just have to sit back and watch as Google smears them with fake extensions that steal their good name pic.twitter.com/3Tnv4NtY9t
— SwiftOnSecurity (@SwiftOnSecurity) October 9, 2017
The 37,000 infected users probably hope this public shaming further motivates Google to buffer the Chrome store's verification process. After all, malicious developers will only get more inventive if the problem isn't fixed.
TopicsCybersecurity
(责任编辑:探索)
 Carlos Beltran made a very interesting hair choice
Carlos Beltran made a very interesting hair choice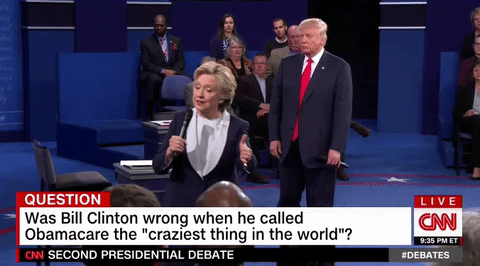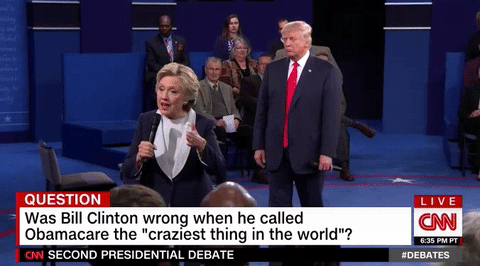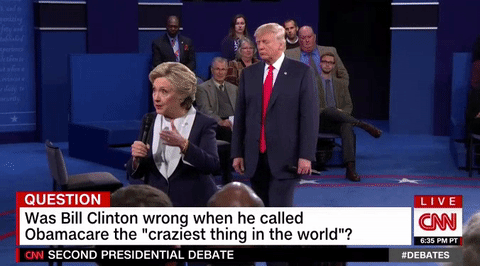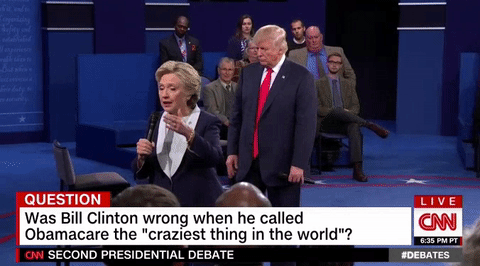 Trump lurks like a hungry ghost behind Clinton during entire debate
Trump lurks like a hungry ghost behind Clinton during entire debate 5 fascinating details from the 'Walking Dead' comics panel at NYCC
5 fascinating details from the 'Walking Dead' comics panel at NYCC Bob Dylan wins Nobel Prize in Literature
Bob Dylan wins Nobel Prize in Literature Did our grandparents have the best beauty advice?
Did our grandparents have the best beauty advice?Did our grandparents have the best beauty advice?
 Do our grandparents really know what's best?They're older and wiser, and they have no shortage of ad
...[详细]
Do our grandparents really know what's best?They're older and wiser, and they have no shortage of ad
...[详细]Xiaomi cashes in on India's festive season, sells over 500,000 smartphones in 3 days
 After two years of its stay in India, Xiaomi has learned a thing or two about the country’s fe
...[详细]
After two years of its stay in India, Xiaomi has learned a thing or two about the country’s fe
...[详细]Explanation for damaged letter will make you grateful for email
 LONDON -- Nobody likes to receive a letter that's both damaged and delayed, but when it's accompanie
...[详细]
LONDON -- Nobody likes to receive a letter that's both damaged and delayed, but when it's accompanie
...[详细]NBA Vine alert: Blake Griffin nails opponent in the jaw with a shoe
 To quote the great Austin Powers: "Who throws a shoe? Honestly!"Well, Mr. Powers: NBA star Blake Gri
...[详细]
To quote the great Austin Powers: "Who throws a shoe? Honestly!"Well, Mr. Powers: NBA star Blake Gri
...[详细]Olympics official on Rio's green diving pool: 'Chemistry is not an exact science'
 The diving pool for the Summer Olympics mysteriously turned green this week in Rio de Janeiro, then
...[详细]
The diving pool for the Summer Olympics mysteriously turned green this week in Rio de Janeiro, then
...[详细]Aussie police are already arresting creepy clowns after multiple sightings
 The appearance of creepy clowns has been reported across the U.S. in recent months, starting in Sout
...[详细]
The appearance of creepy clowns has been reported across the U.S. in recent months, starting in Sout
...[详细]Desert Trip: The Rolling Stones cover the Beatles, and other End Times signs
 INDIO, Calif. -- In a year when music icons of a certain age have been leaving us by the increasingl
...[详细]
INDIO, Calif. -- In a year when music icons of a certain age have been leaving us by the increasingl
...[详细]Android 7.1 Nougat won't bring Assistant to everyone
 If, after seeing all the software goodies on Google's new Pixel phones, you hoped that some of those
...[详细]
If, after seeing all the software goodies on Google's new Pixel phones, you hoped that some of those
...[详细]This 'sh*tpost' bot makes terrible memes so you don't have to
 The internet is awash in trashy memes just waiting for your late-night retweet spree. Why waste prec
...[详细]
The internet is awash in trashy memes just waiting for your late-night retweet spree. Why waste prec
...[详细]Aussie police are already arresting creepy clowns after multiple sightings
 The appearance of creepy clowns has been reported across the U.S. in recent months, starting in Sout
...[详细]
The appearance of creepy clowns has been reported across the U.S. in recent months, starting in Sout
...[详细]Fake news reports from the Newseum are infinitely better than actual news

NBA Vine alert: Blake Griffin nails opponent in the jaw with a shoe
